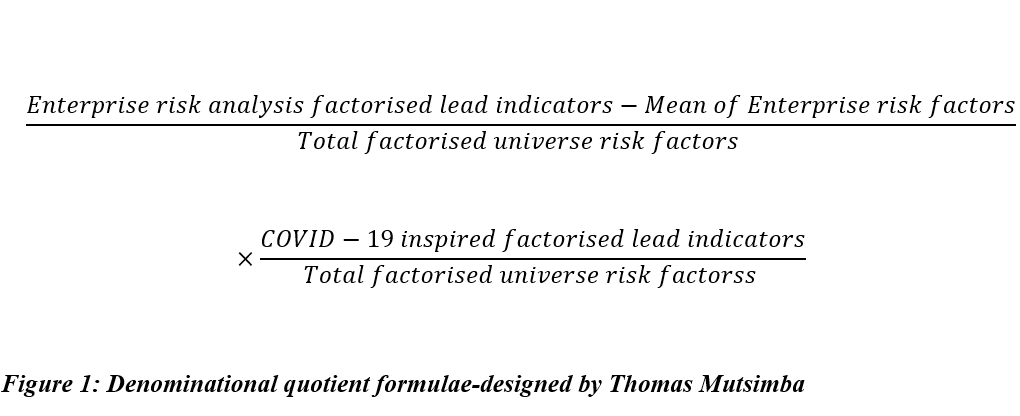
Written by Thomas Mutsimba, an Enterprise Risk Management Professional, with specialist endowment in advanced actuarial analysis and advanced forensic analysis©
Visit ThomasActuarialanalysisworld Blog for more cutting edge insights @ https://actuarialanalysisworld.finance.blog/
Business and Information Systems environments may become convoluted and or multiplexed by using multi-sets of programming languages. This is especially in dynamic information processing environments where the demand for utilities become critical to drive business analogies of different datum structures. It is important to note that programming is an information systems’ engineering tenet that sets the pedestal of jargonated architectures hidden behind user interfaces. The sets of programming languages de-sensitized via de-jargonation methodologies serves to ensure security. This security is information security. It is not just an end product of information systems engineering, but it is a fundamental tenet that through modelling sets, become the centre stage of servicing the information and communication systems environment.
Multi-programming sets of languages are now being used because of highly transformative business environments. These are used to engineer data formation tablets. These data formation tablets are a tenet of actuarial modelling. In this article, I explore how actuarial modelling centres information security models to service a multi-programming language universe. Programming is the definitive degeneration of a set of instructions that compute algorithm set motion dynamics. This programming sets the tone of execution of algorithmic instructions using indexed sequencing and motion sensory dynamics.
Actuarial modelling in Information security models
Actuarial modelling comes in via the information security models. The former refers to the input fundamentals formation degenerating the sector-merged formation of a variety of components in a system. Actuarial modelling is convoluted in the sectoral datum structures and it is discernible through actuarial formation analytics. The thrust of this article is to expound on the actuarial formulants analytical datum perspiratory dynamics as they are deployed, via centerage de-jargonates in the algorithm sensory motion dynamics. Entities seldom expound the multi-programming language sets actuarial formation analytics because of de-sensitization points or points of interest. Points of interest is where jargonates of programming datum structures convoluted in tenets of indexing, looping, concomitant error jargonated analyticals centre information security structural systems.
The Knowledge Index
This article is an uncouth article, expounding knowledge convoluted in actuarial forensics formation dynamics of programming science that any information security risk or model manager would have advantage over peers.
Drivers of Multi-language programming analytics
Via a centerage knowledge index programming language analytic, the following are drivers of multi-language programming proffering actuarial index central formation knowledge base extrapolated to a multi-programming sets:
- Programming centerage identification sets.
- Gentric Actuarial Distributive formation.
- Programming Engineering Datum analytical formation.
- Center of Index Hierarchical programming.
- Formulants of multi-programming assurance structures.
- Information Security-Multi-programming language conclusionary assurance.
Programming Centerage Identification Sets
Formulation program indexing formation refers to the programming release construction of indexing. Indexing refers to the formation of datum grouping methodologies, convoluted using set quantum fixed framework identification formulants. This formation centres the various and or multi-programming powered datum pinned structures de-jargonated under information system structural systems. The formulation program indexing formation in a multi-programming environment is a key depicter of common parsing language identification sets. Why is that so? It is so because of the following:
- Indexing is an advanced actuarial degenerate format.
- Program indexing ferments the information security models to compact link different datum structures.
- Program index formation is a sensitized datum-node structure utility. What is a sensitized datum node structure utility? A sensitized datum-node structure refers to decryption of information systems structural systems that are convoluted by information security as a model of nodal linkage between the information system and the technological universe. Program indexing, a tenet of actuarial formation in multi-programming environments copulating and or serving the centre of the program. Information security program delineation enables the identification of structures. These stratums linked via node datum de-jargonation technically provides a basis of actuarial measurement of pervasiveness of information systems structural depictors of common language parsing identification formulants.
- Program indexing formation in multi-programming environments deployment of actuarial formation is a key driver of information security modelling centerage. Information security modelling centerage in this case is a sequestration technic formulator. Jargon centric stratums are looping technics meant to link different functionaries. Programming in multi-programming environments results in formulator-need sequestration mechanisms. These are advanced actuarial formation technics that cause information security sensitivity analytics to commonality formulate to cause a differential quotient measurement base. What is a differential quotient measurement base? It is information security model deployment technics using formulants built on five (5) de-jargonates. The five quotient de-jargonates are:
1.Programming sensory parsing measurement.
2.Programming language performance indicator measurement.
3.Programming datum structure meshing efficiency code.
4.Programming frameworks: the centerage efficiency identifier.
5.Programming languages indexing centre. - Identification sets of the parsing stratum must be an Ajuncture trait decipherable. What is an ajuncture trait decipherable? This is a line-by-line sensory language notation . How is this notation constructed? It is constructed using language tabular symbols or language quotient notation identifiers. Using utility core modular language parsing mergers, a combination construction interface is de-populated over commonality identification sets. The Actuarial formation utility will extricate analytics over the directory building utility. The directory-built utility forms the program binary base index linkage to analytics linked to the directory building utility. The Actuarial analyst of datum structures in the multi-programming environment creates profiling analytics that are directory input language commonality parsing identification sets.
Centre of Programming parsing utility
What is the centre of Programming parsing utilities? This refers to the centerage of a component of a programming tenet hosting a utility, a program, an enabler of the extrication of actuarial quantum director. Where is this centre located in a multi-programming environment?
Information security becomes critical as its actuarial formatics must centre the jargonated architectures along this centre. In a program, this centre is hosted via an interpreter desensitizer of the parsing utility language. The interpreter translates the extrication formulants via commands that are built through the command line prompt. The command line prompt envisaging or built to set jargonate combiners of multi-programming environments ridden with multi-registry datum structures, parsing utilities can enter at the actuarial formation of information security components datum perspiratory encryption dynamics.
The Actuarial formation of centerage analytics
The actuarial formation of parsing centerage analytics are real. They are performed using key analogue analytic record breaks created each time a parsing command is executed via the centerage command line prompt. The centerage command line prompt directs the record hits via actuarial squared deviation of binary formation base indexing. The squared deviation lists or ranges or notates record breaks using a notation language-built tab, built in the command line parsing enabler.
Jargonated at actuarial squared deviation aesthetics binary language hits, concomitant formulants correlate via extrapolation of binary language base mathematical in formulant correlator. What is this? This is the mathematical efficacy set interpreter of centerage analytics factorial lead indicators.
How is this mathematical efficacy set interpreter of significance in multi-programming language environments?
This is of significance as it attenuates the effective programming bits (binary bound) towards the actuarially formatted combining of multi-programming language towards the centerage index. The centerage index will be a key actuarial measure of information security amplification of key datum structure jargonation to protect multi-server environments where data base registers are held. In formulant reporting of assurance over information security will be reported using this Centerage Assurance Index. This is the age of multiple programming environments that is at bay. The Actuarial knowledge I write is advanced techno-actuarial analysis built in actuarial forensics formation.
Utility Index Relational Identifier
Utility Index Relational Identifier is an actuarial measurement technic that sequestrate information security model requirements via creation of utility built in functional protagonistic datum index contributory identifier. It is a de-basing mechanism that is mathematically deciphered.
How is the Utility Index Relational Identifier mathematically deciphered?
Utilities are used in a variety of programming languages. Multi-programming environments with a quest of centring information security models drive programming language binary formulation centre index. Using advanced actuarial formation analytics, we dexterize the binary datum formatting index. Dexterization is done as follows:
- Utility censorship mode dexterizes at datum process of extrapolation deciphered at extraction command line.
- Dexterization is a formulant actuarial extrapolation exponentiation using binary language indexing. Binary language indexing is used as an actuarial input fundamental via information security centerage. The index is a bit recessionary expansionary laxative range formulator set to attenuate dexterization extrapolated quest. Nudging sets of utility indexing relational identification fosters the mathematical deciphering tenet.
- Utility relational quotiency is a software algorithm acu-frequency maximization tenet. What does it mean? It means utility formation of actuarial technics used to de-jargonate datum-pinned structural relational functional denominatory is deciphered via this quotiency. Quotiency of this nature is also an information security de-jargonated analytical. The actuarial formation of the components of the centerage index pinned actuarial technics decentralizes the mode formation and or movement dynamics.
Control of this utility tenet moves in tandem with registries’ hive record counts analyticals. What does it mean? It means registry hive pinned analytics are essential for utility information systems analytics impact on the multi-programming environment. The multi-programming environment stands as a utility hosting conduit that must facilitate information security peripheral analytics. What does this mean? Information system peripheral analytics refer to the study and determination of information security deciphered datum pinned perspiratory input and output dynamics with an impact analytic of this nature on the multi-programming environment. - Dexterization is actuarially centred and multiplexed. This refers to the use of the determined actuarial binary indexed actuarially centred de-jargonation technics. The de-jargonation technics here unravels the quest for centring information security in multi-programming environment.
Deviationary Program Inconsistencies
This is synchronization-asynchronized actuarial formatic input variant analytics. Information security models measured at the entrance denturity pervasion datum-pinned structures affect the multi-programming environments. Inconsistencies posture themselves at the rate of development algorithm index. The development algorithm index is a multi-programming environment network structured and deciphered actuarial formation movement dynamics.
Organizations or utilities today must format the sensationalization de-jargonation input fundamental algorithm indexing sequencing emanating from deviationary program inconsistencies that arrive via parsing breaks inconsistent concomitant inefficiencies. Parsing breaks inconsistent concomitant inefficiencies refer to the following:
- Parsing formulation sets are sequestrated at language index combination factors which are distributed in multi-programming environments at centerage index actuarial analytical formulatory utility decipherables. The sets being referred to here are sets of record break extrication mechanisms. Record break extrication mechanisms of the parsing algorithms are released in the multi-programming merging utilities using an actuarial technic known as Censor form de-jargonator. A Censor form de-jargonate can decipher frameworks used to implement parsing algorithms within a multi-programming environment.
- Actuarial technicalization of parsing co-variants. What are parsing co-variants in multi-programming environments? Parsing co-variants are multi-programming language environments extrication leverages that are used to release algorithm de-jargonation analyticals. What does this mean? De-jargonation analyticals as an input into the information security model or models of such an environment require parsing co-variants. Under actuarial formation co-variants is a dual binding efficient frontier built on language formation index.
- Parsing breaks-The analytical consummation set. The analytical consummation set refers to the role that the envisaged and or formatted, deployed information security model plays in securing the parsing utilities. In multi-programming environments parsing utilities are susceptible to dysfunctionality injectors. Dysfunctionality breach injectors refer to malware and or malicious code that works with de-sensitizing indexes of datum-pinned structures.
Depictors of Program de-sensitization Indexes
De-sensitization indexes in multi-programming environments refer to areas and or datum pinned indexed structures where there is an ability to introduce fault lines that can tamper with the de-jargonation analytical functionaries. Formatting information security models in such an environment may be a mammoth task.
Using actuarial techniques there are depicters of de-sensitization indexes. Program structures run against multi-programming environments operating systems registries structures may indicate comparative analytics of movement dynamics as the multi-programming environment is formatted.
Sensationalized Amplified Algorithm index partitioning datum
This refers to plotted algorithm trace of breakage in looping formatics that are actuarially determined at entrance of meshing indexed datum pinned structures. Using actuarial and forensic analysis merged technics, the amplification mode is deciphered using the following methods:
- Amplification of indexed stratum record breaks.
- Actuarial deviation technics of datum-pinned indexed structures from different programming environments.
- Command line extraction code of actuarially de-sensitized datum indexed structures.
- Record extraction and formation analytics.
The Depicters of Program de-sensitization indexes are:
- The Leverage formation actuarial analytics.
- Censorship mechanism of algorithm interchange or interchange between multi-programming environments.
- Information security model actuarial formation mode.
- The troughing and centring of trend indexed datum-pinned structures.
- Actuarial formation centerage trend analytics.
- Actuarial modelling of information security sensationalization.
- Datum Governance centerage technics.
- Data build banks.
The Looping conundrum directional formulator and or depicter
This section deals with the formulators of the looping conundrum. The Looping conundrum represents challenges experienced in a multi-programming environment. The looping conundrum in such an environment comprises the following:
- Structurally damaged data banks.
- Looping utilizer of utilities.
- Program structures indexes and desensitization indexes overpopulation.
- Programming source code meshing in multi-programming environment.
- Actuarial formation of looping technics.
- Hierarchical datum base structures.
The Looping conundrum directional formulators refers to the actuarial formation input enablers of information security model pinned director of looping. Looping is a de-sensitizer formatic mode. What does this mean in light of multi-programming environments? It means that looping is done at actuarial leverage centre formation of de-jargonated input and output fundamentals. The formulators serve as de-jargonates of formulants. The formulants being referred to here are the information security structural systems combination outcomes that are calculated using built in actuarial analysers.
Today’s Organizations or Entities
Today’s organizations and or entities serve as the sequestration site where coding is done at data banks information security formatted structures. The format here is deciphered using deep actuarial laboratory sets hosted in registry structures built using intelligence of utilities co-listing registry hives to test the formatic input decipherables.
The looping conundrum formulators include:
- Sets of perversion of program indexed structures destined for the multi-programming environment.
- Actuarial centerage efficiency buoyancy.
Sets Meshing Methodologies
Sets meshing methodologies are key programming identification methodologies. Since this item is being elucidated to emphasize the importance of combining or merging multi-programming environments, sets are identified as information security structural systems. One cannot exclude the importance of security. The sets meshing methodologies differ. It is not a one size fits all mechanism. Some of the programming sets meshing methodologies include:
- Registry meshing utility analytics.
- Environmental datum structures commonality meshing.
- Algorithm meshing analyser.
- Standardised actuarial formation notation of information security models.
Gentric Actuarial Distributive Formation
Gentric actuarial distributive formation refers the datum sensitivity-pinned notation of key input and output fundamentals of the multi-programming environment distributive systems. In a previous section, I covered the centerage identification sets. Without these centerage identification sets one would not be able to de-base to Gentric actuarial distributive formation. There are many gentric actuarial distributive formation mechanisms.
These mechanisms are built on the partitioning index of information security models and actuarial formation. The partition index is used in advanced actuarial formatic compartmental efficiency dynamics. These efficiency dynamics are used in multi-programming environments. The formatics of compartmental efficiency in multi-programming environments include:
1. Program motion velocity centerage.
2. Algorithm denturity indexed structures.
3. The generation of a multiplexed multi-programming environment registry structures.
4. The genetic code of multi-programming environment.
5. Formation efficiency datum line-centerage index.
Program Motion velocity centerage
This is the measurement index in the multi-programming environments that is used to de-jargonate movement dynamics that are a capitulation of distributive formation analytics. Gentric actuarial distributive formation can determine the velocity centerage. Velocity centerage is determined by a myriad of different factors some of them attributable to information security models at hand. The factors include:
- Velocity quantum formulants of velocity centerage.
- Actuarial formation program datum structures linkage.
- Actuarial measurement bases used to decipher the motion dynamics in multi-programming.
- Actuarial formation of datum perspiratory dynamics.
Algorithm Denturity Index Structures
Algorithms not appropriately written are measured using Denturity index structures. Using standardized efficiency frameworks denturity index lists factorial lead indicators that need to posture dentures. Information security models use de-sensitization indexes.
The Generation of multiplexed multi-programming Registry Structures
Gentric actuarial distributive formation also noted in multiplexed multi-programming registry structures refers to inter-twining and interweaving registry structures. How are such registry structures deciphered? This requires gentric actuarial formation technics hence the reason we look at actuarial distributive formation. Actuarial distributive formation comes in a variety of formats. Listed below are the formats:
1. Information security distributive centerage of actuarial deciphers.
2.Language centerage index formation.
3. Actuarial formation of programming language “comma”.
4.Separators utilities de-jargonates.
Information security distributive centerage of actuarial deciphers
This is a gentric actuarial formation that crystallizes in multi-programming environments. The focus is on the distributive mechanism. Information security distributive centerage of actuarial deciphers refers to the rectum deciphered channel of penetrative datum pinned structures that sets the stage for a malcontent baseline structure that redirects the mode or direction of the multi-programming environment. The centerage of actuarial deciphers is deciphered via identification of information security factorial lead indicators. A centre of excellence framework-built database of these indicators is photo-stated live at the multi-programming environment distributive monitoring. The dashboard takes host to the following:
- Actuarial centerage centre of formulatory data comprising of modelling object pinned datum structures.
- Censorship technics of monitoring factorial lead indicators.
- Frequency of program denturity along the computed trendline extrapolated over the entire multi-programming universe.
- Actuarial formation analytical factors which differ with each multi-programming environment.
Language Centring Index Formulation
Programming languages used in multi-programming environments are a key component in multiplexity of registry structures. The Registry for each programming environment servicing as an input is a jargonated architecture component of an information security model. These programming languages are employed in what is known as Language Centring Indexing Formation.
Language centring index is a language used to build programs and or an algorithm. The components of these languages must be partitioned using the language utility index de-jargonation.
How does the language utility de-jargonation work?
It is built with the programming database linguistics of the advanced algorithm reader. Built for multi-programming environments actuarial technics, formation sectors are built to aggregate, analyse, and evaluate as well as monitor and report. An index designed, written using actuarial mathematics centerage circulator or iterator, runs throughout the multi-programming environment plotting datum trend performance. Centerage of the languages is a categorised mathematical algorithm built to accentuate compilation of reportables. The centerage is calculated using Variance Stochastic modelling. What is variance stochastic modelling?
Variance Stochastic Modelling
This is Actuarial modelling used in multi-programming environments to format censorship of information security distributive centerage. Constructed via a benchmark programming language list of common and unique registry structures, behavioural trends and performance as registry structures, be it meshing or pervading are deployed into the multi-programming environment, each injection identifier of the security built in decipherable is allocated and or scored at a framework whose factors are squared notated characteristics.
The squared component superscript is a dual functionality actuarial fundamental identifier of key input and output fundamentals as noted by the information security model of components or information security structural systems.
Stochastic Model Sensitization Sectors of Programs
What are these sensitization sectors? Information security models are convoluted in program storage memorability. RAM conscientizer track constantic merging of sector rotation efficiencies. What is this? Multi-programming environments host multiple servers deployed to the production server. The Production server in turn hosting hardware storage capacities has a capability via program development utilities to develop and deploy a stochastic model sensitization sector.
This sensitization sector serves the de-juncture multi-programming conversion index. A de-juncture multi- production for conversion index is measured at collectibles of RAM-hard disk rotation access juncture points of interactions in the multi-programming environments. The points of interest are hits of interactions between the main servers hosting multi-programming environment data. On each hard disk sector, the stochastic sensitization sector data recorded in operating system registries are a myriad of classes which also includes RAM access, additions, deletions, alterations, registry structures, formatic additions, rearrangements and restructuring tenets. Measured at an index broken down into a framework, scores are allocated at each hit, points of interest are iteratively plotted at development milestone intervals. These specific points plotted at certain points are compared against the stochastic modelling target and or forecasted model objectives
Actuarial Formation of Programming Language “Comma”
What is the actuarial formation of programming language “comma”? This refers to the information security modelling components unique characteristics. The comma refers to misplaced program object structures. This occurs in highly advanced program structures in multi-programming environments.
Separator Utilities de-jargonates
Separator utilities used in multi-programming environments refer to information security modelling actuarial formation used to separate different program object structures. The separator utilities serve as an actuarial formation decipherable mechanism technic These in multi-programming environments are critical algorithm de-jargonators.
Programming Engineering Datum Analyticals Formation
These are datum analyticals formation structures focusing on engineering programming in a multi-programming environment. Datum analyticals in such environments are built on actuarial formation structures. An Actuarial analyst must know the actuarial fundamentals of programming engineering that are input into the modelling of datum analyticals. The fundamentals I am referring to are as follows:
- Program code sector analysis.
- Datum structures pinned on object orientation.
- Structural analytics using gentric outlying orientation factors.
- Programming analytics at each multi-programming environment.
- Actuarial centerage indexing as a key datum analytical formation.
- Actuarial formation of analyticals de-basing to key input and output fundamentals in a multi-programming environment.
- Period driven program sector resource and Sector driven analytics and reporting.
Centre of Index Hierarchical Programming
This is an actuarial formation technic built on advanced information security modelling centre of indexing hierarchical programming. This is Programming in multi-programming environment that follows programs and or software model hierarchies that are formatted using actuarially plotted centerage. The actuarially plotted index centerage is plotted and or formatted based on program structures being built.
Why is this of significance to multi-programming sets of languages?
The centre of index hierarchical programming is meant to ensure optimization of a chosen information security model and or models. This is a relegation of de-basing actuarial formation perspiration dynamics meant to centre the index hierarchy. Organizations and or entities involved in use of multi-programming sets of languages must employ actuarial technics to centre information security to service such a language universe. The factorial lead identifiers of the centre of index hierarchical programming that direct the modus operandi include the following:
- Hierarchical objects set up frequencies using actuarial notation to classify and or categorize.
- The notation methodology of information security modelling tenets.
- Sense structure of actuarial technics motion built in sensory utility de-jargonation.
- Mathematical relational identifiers built on binary formation index of data structures at different levels and or hierarchies.
- RAM sectors identified at actuarial formatic input.
- Formulants structural analysis of multi-language sets.
Formulants of Multi-programming Assurance Structures
Multi-programming sets of languages used to build multi-programming environments employed or supported by actuarial models that centre information security use a certain modus operandi. The modus operandi being referred to are formulants or key input methodologies that de-jargonate the assurance structures. This becomes imperative to give assurance or provide multi-programming assurance structures. This is a gap that always exists in Board, Audit and Compliance Committees due to technically convoluted jargonated architectures that must be broken down and or unravelled for the benefit of Governance structures.
There is an amplified assurance structure jargon. This is frame worked multi-programming structure, assurance structure that is sensationalized methodology. Sensationalized is used here to formulate the importance of period-banked analytical datum frequencies. Data is always a critical component or input for assurance structures. Stated below are the formulants of multi-programming assurance structures:
- Jargonated architectures of multi-programming languages.
- Key programming language indicators as deciphered via the centerage index.
- Formulated reportables built from actuarial formation of information security models.
- Risk Modelling built via languages securitization.
- Denturity of language sector analytics.
- Formulants indexed analytical structure.
- Assurance structures modelling tenets.
Information Security-Multi-programming sets of languages assurance
This is an alignment tenet, conclusionary in nature that depicts how the multi-programming sets of languages gives assurance to the multi-programming quest through centring executed by actuarial formation technics. This assurance is built on core-modular tenets that must give satisfaction to the entities Board, Audit and Compliance Committees. The four core modular tenets are:
- Information security model actuarial formation testing.
- Key Actuarial Index indicators.
- Gentric Analytics. Centerage reportables.
- Multi-programming sets of languages performance indicators.
This is the information security model centring of actuarial formation as a base formation that supports of use multi-programming sets of languages in a multi-programming environment. Organisations and or entities lag in this area effectively perspiring gaps in information security multi-programming environments assurance centring for the Boards and their governance committees.
Disclaimer: All views expressed in this article are my own and do not represent the opinion of an entity whatsoever, with which I have been, am now, or will be affiliated with. ©